Multi-Factor Authentication with Duo Security
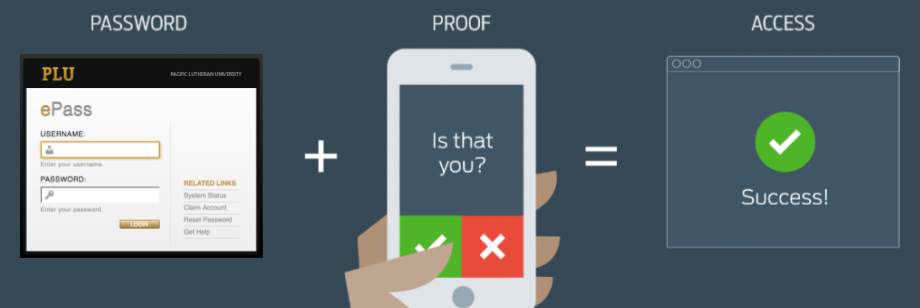
In order to better protect your ePass account and its access to your personal and institutional data, Information & Technology Services provides an additional security feature for PLU ePass accounts called multi-factor authentication. Many PLU web-based services and accounts that may have access to sensitive data are enabled to use multi-factor authentication. This means that in addition to providing your ePass username and password at the time of logging in, you will be required to provide an additional piece of verification before you are allowed access. Most commonly, this additional step will be done via a notification sent to your mobile phone or another device in your possession. This added security feature makes it much more difficult for unauthorized users to access your account using stolen credentials, as it asks you to verify your login using a device only you possess. The added security is an increasingly important step in keeping your personal information and PLU’s institutional data secure.
Why Use Multi-Factor Authentication?
Higher education institutions have developed single sign on accounts, such as the PLU ePass, to make it easier for students, faculty, and staff to access institutional services, data, and resources using a single username and password. However these accounts are increasingly being targeted by attackers trying to gain access to sensitive personal and organizational information. If someone mistakenly provides their credentials or otherwise has their account compromised, those credentials can be used to sign in from anywhere to collect any data that the account has access to. Significant damage and loss is possible such as:
- Financial Fraud – Hijacking paychecks or tuition refunds to the thief’s accounts.
- Identity Theft and Tax Fraud – Accessing personal and/or family information such as Social Security numbers from tax forms such as W4, W2, 1095-C, or 1098T.
- Financial Aid Fraud – Defrauding an awarding agency or the federal government.
- Student Grade Hacking – Using USB keyloggers to capture faculty login credentials and change grades.
- Institutional Data Access – Accessing restricted institutional data.
For more detailed examples of risks, view the FAQ Why is multi-factor authentication necessary for my account?
The good news is that with multi-factor authentication enabled, many of these risks can be reduced or eliminated. For example, after Google rolled out multi-factor authentication to over 85,000 employees, no instances of compromised accounts were reported the following year.
Enabling Multi-Factor Authentication for Your PLU ePass Account
Please view the Getting Started page and video tutorial below to learn more about the multi-factor login process, how to set up your account, and how to get help if you run into issues.
Frequently Asked Questions
PLU accounts are increasingly being targeted by attackers trying to gain access to sensitive personal and organizational information. If someone mistakenly provides their credentials or otherwise has their account compromised, those credentials can be used to sign in from anywhere to collect any data that the account has access to. Multi-factor authentication significantly limits unauthorized access, as someone would need both your credentials as well as having access to something that only you would have possession of, such as a mobile phone, to get in. For this reason, multi-factor authentication is being implemented for PLU faculty, staff and student worker accounts. Students that have not worked on campus as student workers may also enable multi-factor authentication through Duo Security.
Examples
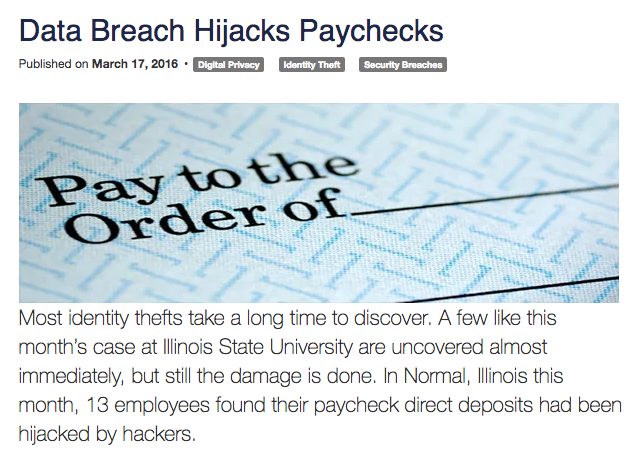
Paycheck Hijacking – See Data Breach Hijacks Paychecks
Student Grade Hacking – See Easy-to-get hacking device puts KU professors’ information in student hands
More Info
The current supported options for multi-factor verification with Duo Security are:
- Mobile phones: Responding to a push notification sent to the Duo Mobile app, generating a one-time passcode in Duo Mobile, or triggering a phone call or SMS message and following login prompts (only available for some accounts).
- Tablets or Apple Watches: Using the Duo Mobile app options available for these devices.
- Saved Passcode: Entering a passcode from a list previously generated and saved as a backup.
- U2F Token: Linking a U2F authentication key (must be purchased separately) with your account and having it plugged into the USB port of the specific device you are connecting from. Contact the I&TS Help Desk for details regarding obtaining a U2F token.
When you are signing into one of the services that requires multi-factor authentication, you should see a check-box at the bottom of the screen that says “Remember me for ## hours/days”. Once this box is selected, you will not be asked to provide the secondary verification from that browser on that particular device for the time listed. Available time frames provided can range from 12 hours to 1 month and will be automatically determined for you based on your account and the specific level of data access you have.
Multi-factor authentication is available for all PLU employees and students. Faculty, staff and student workers are required to sign up for the service by the November 28th 2018 deadline, while all other students currently have the option to sign up for the service to add additional security to their account.
Once you have signed up with a Duo Security and enabled it on your PLU ePass account, you will be unable to revert back to the single authentication method. All PLU employees and student workers will be required to have multi-factor authentication set up for their accounts by November 28, 2018. The opt-in period is offered simply to provide a smoother transition for those individuals who are ready to make the transition.
If you are unable to access your enrolled device to complete a multi-factor login with Duo Security, and you don’t have a backup phone defined, you have the following options:
- Use a previously generated backup code that you saved (see Generate Backup Codes page.)
- Contact the I&TS Help Desk at 253-535-7525 to assist with getting temporary access or to add a replacement device to your account. When calling, please be prepared to answer questions to verify your identity prior to making any changes to your account.
While the most convenient option for multi-factor authentication is normally linking your account to a mobile phone, there are a few other options that are available to you. The other supported authentication devices are:
- Tablet or iPad: Download the Duo Mobile app and have notifications pushed to the device, similar to the mobile phone option.
- U2F Token: Link your Duo account to a pre-purchased device that you carry with you to connect to the computer and authenticate with when logging in. Contact the I&TS Help Desk for more information.
- Landline Phone (only available for some users): Receive an automated phone call when attempting to log in and follow the instructions provided.
Currently all single-sign-on (SSO) connected applications (e.g. most web sites protected with ePass) utilize multi-factor authentication, regardless of the particular service it provides. During the initial deployment of this service, other services that use ePass credentials, but not through SSO (e.g. windows login on your desktop or windows login on lab computers) will not use multi-factor authentication. Over time we do expect many of these systems to either move to SSO or have multi-factor enabled, but no specific timeline is currently available.
The information collected by Duo Security during the multi-factor authentication process is similar to information that might be collected by web sites as you browse web pages. Duo does not collect detailed location information such as GPS coordinates of your mobile device. Specific information about what data is collected can be found on Duo’s Privacy Policy page.